A client of ours recently began site migration to Magento 2 and had just begun the onboarding to Scandiweb’s 24/7 Magento support service. Even though the onboarding process was not completed yet, our team got an urgent message and rushed to try and help. Here’s what went down.
The client needed backup against DDoS attackers they’ve been fighting off for a few days. After discussing the situation and options, we learned that the client is currently using Sucuri as their security layer. Since Sucuri has limited options to prevent the DDoS, we suggested switching to Cloudflare and recommended adding ReCaptcha to the form that is being attacked.
Soon after, attackers noticed the switch and tried to change up the strategy with no luck. Here’s a message we got from the attacker (we took it as a compliment):
“Cloudflare is it?
Already given up on Sucuri? You have noticed the drop in Google rank have you?
So, where will you go after we have triggered Cloudflares site protection system?
Pay and we stop attacking your site, you are losing massive amounts in sales EVERY day we persist
We will NOT leave [website name removed].com alone until you either pay for OUR protection or you go bankrupt. [Website name removed].com WILL be made an example of if you do comply
Cloudflare is not impassible for us
You have been warned
REvil
This is OUR Dominion“
The next day, the DDoS attack on the page was attempted again. Cloudflare detected it and blocked it in no time, increasing the client’s trust and confidence in the security platform and our knowledge.
It was the biggest DDoS attack we’ve seen for our clients so far – 65 million requests, peaking at 10,000 requests per second. Cloudflare was blocking 99% of malicious traffic automatically, but some smarter bots were going through and degrading site performance. We manually adjusted multiple parameters and implemented rate-limiting for certain paths.
Someone was even coordinating this and making adjustments to our actions. At the end of the day, no malicious traffic was reaching the client’s site. For now.
If you’re curious about how events unfolded – the attackers returned a week later, at 2 AM on a Saturday night.
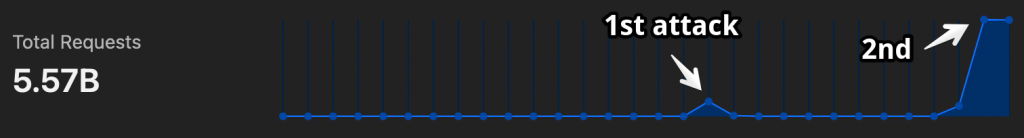
This time the attack lasted three days, during which the attackers sent 6.7 billion requests, peaking at 80,000 requests per second. It took 26 terabytes of traffic just to show them a page with text that they are not welcome here.
The previous wave with 65 million requests with 10,000 at peak seemed tiny now.
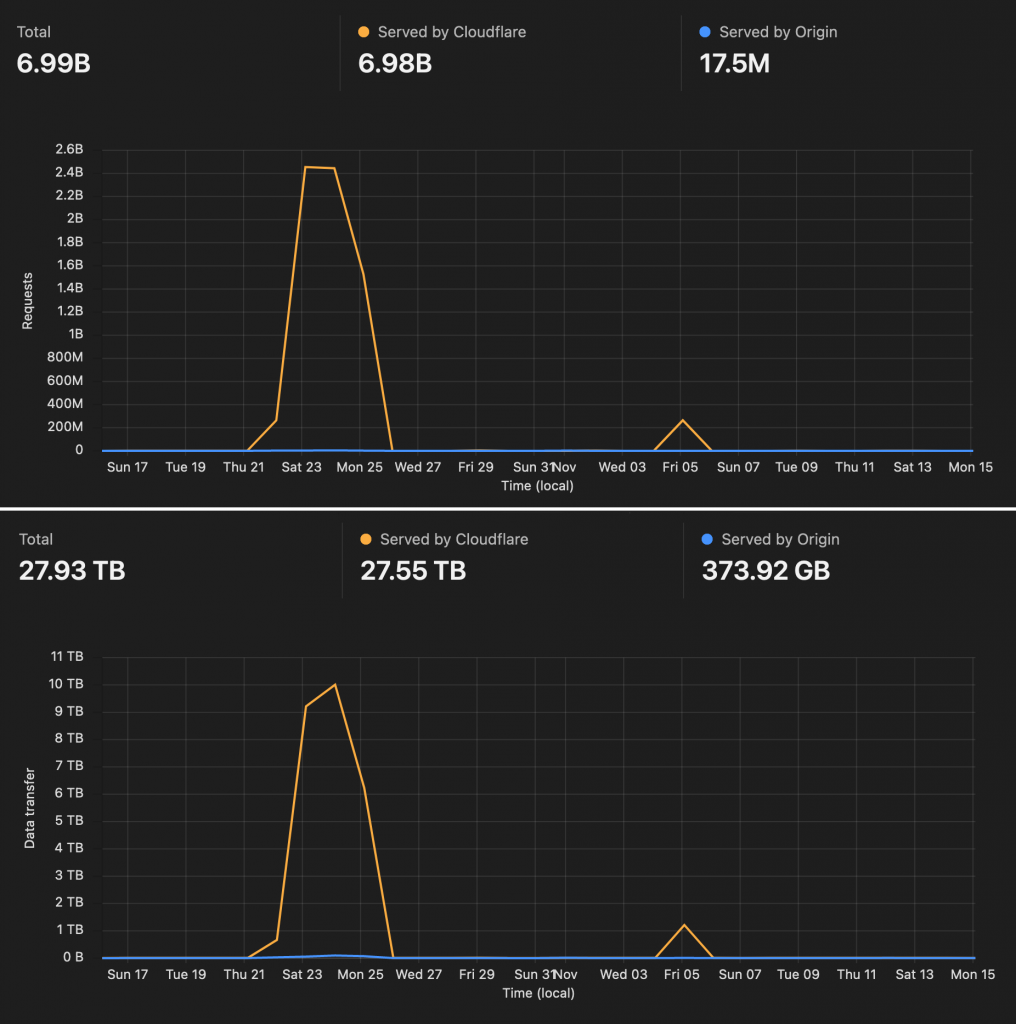
As for our solution – if the first wave was handled by Cloudflare’s 20$ plan, the second wave appeared more sophisticated and required features available only on the 200$ plan, like regular expression matching. Still, we believe it cost more for the attacker.
Need support setting up preventive measures to protect your Magento store from DDoS attackers? Our expert team of developers is ready to help you with that and more. Send us a message or hit the orange chat bubble to get the conversation started today.



Share on: